17
In order to ensure that your business runs efficiently, it is essential to ensure that your network is safe. My own personal experience has shown me the possible catastrophes that can occur as a result of maintaining an unprotected network. It is possible that depending exclusively on reactive technologies such as antivirus software would not be sufficient in the modern world, when instances of data breaches are sadly quite regular. As time has gone on, I’ve grown to understand the significance of remaining one step ahead of any security threats, and this is where vulnerability management solutions come into play as key players.
As someone who has dealt with the aftermath of security breaches, I have seen that waiting for damage to occur before taking action is not the best option. In my experience, vulnerability management solutions provide a proactive approach by finding holes in a company’s system before those weaknesses may be exploited. This allows the organization to take preventative measures. These technologies are not limited to merely detecting possible security breaches; rather, they actively attempt to prevent such breaches from occurring in the future.
It is the capability of vulnerability management systems to assign threat levels to vulnerabilities that have been detected within a system that makes these solutions practically indispensable. Through the use of this individualized threat assessment, IT professionals such as myself are given the ability to make educated decisions regarding which risks should be prioritized. We are able to successfully handle the most essential concerns first, hence preventing possible disasters, if we categorize and prioritize vulnerabilities depending on the severity of their impact.
Best Vulnerability Management Software
Because of this, you should look into the specifics of vulnerability management options to make sure they meet the needs of your business and security framework. This piece will look at the best vulnerability management tools on the market right now and list their most important features to make this process easier. We’ll talk about their strengths and suggest the kind of organization that would gain the most from using them.
| Feature | Astra Pentest | SecPod SanerNow | Indusface AppTrana | Invicti | Acunetix |
|---|---|---|---|---|---|
| Deployment Model | Cloud-based, On-premise | Cloud-based, On-premise | Cloud-based, On-premise | Cloud-based, On-premise | Cloud-based, On-premise |
| Scanning Types | Dynamic, Static, DAST, SAST, SCA | DAST, SAST, SCA | DAST, SAST, SCA | DAST, SAST | DAST, SAST |
| Supported Platforms | Web applications, APIs, mobile apps, containers, infrastructure | Web applications, APIs, mobile apps, microservices | Web applications, APIs, mobile apps | Web applications, APIs, mobile apps, single-page applications (SPAs) | Web applications, APIs, mobile apps |
| Reporting | Detailed reports with remediation guidance, prioritization, and exploitability | Customizable reports with vulnerability details, risk scores, and remediation steps | Comprehensive reports with vulnerability details, CVSS scores, and remediation recommendations | Interactive reports with vulnerability details, OWASP Top 10 rankings, and remediation suggestions | Detailed reports with vulnerability details, risk scores, and potential impact analysis |
| Integrations | SIEM, ticketing systems, CI/CD pipelines | Jira, ServiceNow, Slack, Microsoft Teams | Jira, ServiceNow, GitLab, Jenkins | Jira, ServiceNow, GitLab, Jenkins, Confluence | Jira, ServiceNow, GitLab, Jenkins, Slack |
Best Vulnerability Management Software
Tools for vulnerability management find security holes in network and cloud settings, sort them by importance, and then fix them. They do more than just scan for vulnerabilities; they make a full vulnerability map for companies that includes risk scores, reports, and asset discovery. We rated the best risk management tools on a scale of 1 to 10 and looked at their features, pros, and cons to help you find the right one for your team.
Astra Pentest
| Feature | Description |
|---|---|
| Vulnerability Scanning | Identifies vulnerabilities in web applications. |
| Penetration Testing | Conducts thorough penetration tests. |
| Security Reports | Generates detailed reports of security findings. |
| Compliance Checks | Ensures compliance with industry standards. |
I’ve used Astra Pentest myself, and I can say that it does a good job of finding weaknesses and possible entry places for attackers. It can do both automated scanning and human penetration testing, which makes it a complete security assessment tool.
The unique thing about Astra Pentest is its easy-to-use interface, which makes the scanning process simple even for people who are new to hacking. It also works well with other security tools, which speeds up the whole process of security review and saves time and effort.
The Good
- Comprehensive vulnerability scanning.
- Detailed penetration testing capabilities.
- User-friendly interface.
- Regular updates and support.
The Bad
- May be resource-intensive.
- Pricing structure could be clearer.
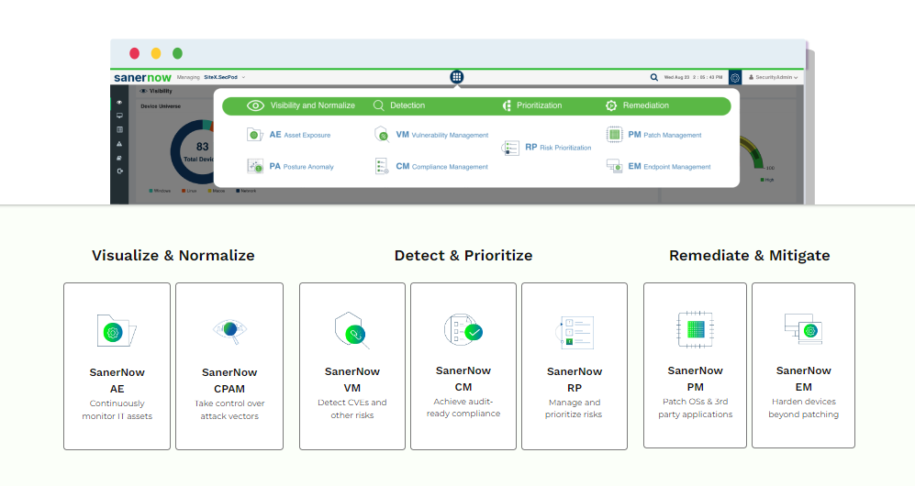
SecPod SanerNow

| Feature | Description |
|---|---|
| Endpoint Security | Protects endpoints from various threats. |
| Patch Management | Manages software patches efficiently. |
| Asset Management | Tracks and manages IT assets effectively. |
| Vulnerability Management | Identifies and prioritizes vulnerabilities |
The next level of vulnerability control is reached with SecPod SanerNow. From my own experience, I can say that it’s more than just a scanning tool; it’s a full answer for managing security holes. SecPod SanerNow gives companies a central location to control all parts of their vulnerability management program.
It does this by offering features like automated scanning, patch management, risk assessment, and remediation tools. Its easy-to-use design makes vulnerability management, which can be hard to do, possible for teams of all skill levels.
The Good
- All-in-one solution for endpoint security.
- Streamlined patch management process.
- Intuitive interface.
- Strong vulnerability management capabilities.
The Bad
- Initial setup may require technical expertise.
- Advanced features might be overwhelming for some users.
Indusface AppTrana

| Feature | Description |
|---|---|
| Web Application Firewall | Protects web applications from attacks. |
| DDoS Protection | Safeguards against DDoS attacks. |
| Threat Intelligence | Utilizes threat intelligence for proactive defense |
| Real-time Monitoring | Monitors web applications in real-time. |
Indusface AppTrana offers a complete way to check for web application security. I’ve liked all of its features while I’ve used it, such as DAST, automated scanning, and human penetration testing.
It does more than just check; it also tests the security of mobile apps and reports on compliance, making it a useful tool for businesses with a range of security needs. Plus, businesses of all sizes can use its free basic plan, which lets them prioritize protection without spending a lot of money.
The Good
- Robust web application firewall.
- Effective DDoS protection.
- Proactive threat intelligence.
- Real-time monitoring for quick response.
The Bad
- Pricing may not be suitable for all budgets.
- Advanced features might require training.
Invicti

| Feature | Description |
|---|---|
| Automated Scanning | Automates vulnerability scanning processes. |
| OWASP Top 10 Coverage | Covers vulnerabilities listed in OWASP Top 10. |
| Integration | Integrates with various CI/CD tools. |
| Reporting | Generates comprehensive vulnerability reports. |
Invicti is the best choice for businesses that need a fast web application security scanner. Invicti is unique because it can find even the most complicated flaws and is very accurate. It has features like proof-based scanning, interactive testing, and DAST. I’ve used it and found it to be an effective way to protect important programs and give me peace of mind against possible threats.
The Good
- Efficient automated scanning.
- Comprehensive coverage of OWASP Top 10.
- Seamless integration with CI/CD pipelines.
- Detailed and customizable reports.
The Bad
- Initial learning curve for setup.
- May not offer as many advanced features as some competitors.
Acunetix

| Feature | Description |
|---|---|
| Vulnerability Assessment | Conducts thorough vulnerability assessments. |
| Network Security | Provides network security scanning capabilities. |
| Compliance Checks | Ensures compliance with regulations. |
| API Security | Protects APIs from security threats. |
Acunetix is a mature and flexible web application security scanner that can be used by businesses of all kinds. I’ve used it and found its automated scanning, manual penetration testing, and DAST features to be strong and effective.
Acunetix is unique because it is easy to use and has a lot of reporting options. This is why cybersecurity experts love it. Acunetix gives you the freedom and dependability to keep your web apps safe, no matter if you’re a small business or a big company.
The Good
- Comprehensive vulnerability assessment.
- Strong network security scanning.
- Compliance checking features.
- Dedicated API security capabilities.
The Bad
- Pricing may be high for some users.
- Interface could be more intuitive.
Making the Right Choice for Your Vulnerability Management Software
When picking vulnerability management software for your business, make sure it meets your goals by keeping the following in mind:
- Complete Vulnerability Scanning: Look for software that can scan your network infrastructure, endpoints, apps, and cloud environments for all kinds of vulnerabilities. Active and passive scanning should both be supported by the software so that it can find vulnerabilities in real time and give accurate security assessments.
- Asset Discovery and Inventory: To instantly find and list all the devices, systems, and apps on your network, choose software that has asset discovery and inventory features. You can check for weaknesses in your whole IT environment by using asset discovery to make sure you don’t miss any devices or systems.
- Prioritization and Risk Assessment: Look at tools that can help you prioritize and fix vulnerabilities based on how bad they are, how easy they are to exploit, and how they might affect your business. To fix the most important flaws first, look for tools that include risk scoring, vulnerability categorization, and threat intelligence integration.
- Customizable Policies and Remediation processes: Look for software that lets you make policies and processes for remediation that are specific to your organization’s security needs and compliance requirements. Customizable policies let you make sure that all of your IT environments follow the same security standards and best practices. Additionally, flexible remediation methods make the process of fixing vulnerabilities faster and easier.
- Integration with Existing IT Systems and Tools: Look for vulnerability management software that works well with the IT systems, tools, and processes you already have in place. This includes security information and event management (SIEM) systems, ticketing systems, patch management solutions, and configuration management databases (CMDBs). Integration features make it easier for security and IT teams to share data, automate tasks, and work together, which increases efficiency and productivity.
- Reporting and Analytics: Look at software that has powerful reporting and analytics tools that can give you useful information and numbers about risk trends, remediation progress, and compliance status. To successfully share vulnerability management metrics with stakeholders and decision-makers, look for dashboards that can be customized, trend analysis, executive summaries, and compliance reports.
- Continuous Monitoring and Threat Intelligence: To find new threats, zero-day flaws, and advanced attack methods, choose software that lets you integrate continuous monitoring and threat intelligence. Having the ability to do continuous tracking makes sure that your company stays alert to new cyber threats and can quickly fix any new vulnerabilities that appear.
- Scalability and Performance: Think about how the software can be scaled up or down and how fast it works to meet the changing security needs of your company. Look for software that can handle large-scale deployments, distributed settings, and a lot of vulnerability data while still running at its best and being reliable.
Questions and Answers
What is the best framework for vulnerability management?
The National Institute of Standards and Technology Cybersecurity foundation offers a useful foundation for the mapping out of a vulnerability management strategy. Identification, protection, detection, response, and recovery are the five key phases that are used by the NIST framework to classify all of the capabilities, projects, processes, and daily activities that pertain to cybersecurity.
Is Nessus the best vulnerability scanner?
To this day, twenty-five years later, we continue to place a strong emphasis on community engagement and product innovation in order to supply you with the most accurate and comprehensive vulnerability data possible. This is done to ensure that you do not overlook crucial concerns that could put your organization in need of protection.
You Might Be Interested In








Leave a Reply